Protecting Your IP Address
When you download files, your computer typically connects to a single source for data transfer. However, in the world of torrenting and peer-to-peer (P2P) networks, you might simultaneously retrieve different segments of a file from multiple users. This process poses a risk: anyone who is either uploading from you or downloading from you can easily view your IP address.
There are numerous reasons to keep your IP address confidential. For starters, having access to your IP can allow someone to pinpoint your general location. Although IP geolocation isn't always precise, it can at least reveal your country or city. In rare cases, this information could make you vulnerable to targeted attacks, such as a denial-of-service (DDoS) attack, disrupting your internet access temporarily.
The more prevalent concern is privacy. Your IP address can disclose significant details about you, like your location and your Internet Service Provider (ISP). Copyright holders often monitor torrent activities related to their content. If they detect your IP address associated with a download, they might send copyright infringement notices to your ISP. This could lead to potential service termination if you continue torrenting. In extreme cases, they might reach out to you directly, demanding hefty fines or threatening legal repercussions for non-compliance.
Moreover, frequent torrenting or streaming can lead your ISP to throttle your internet speed, affecting your overall experience.
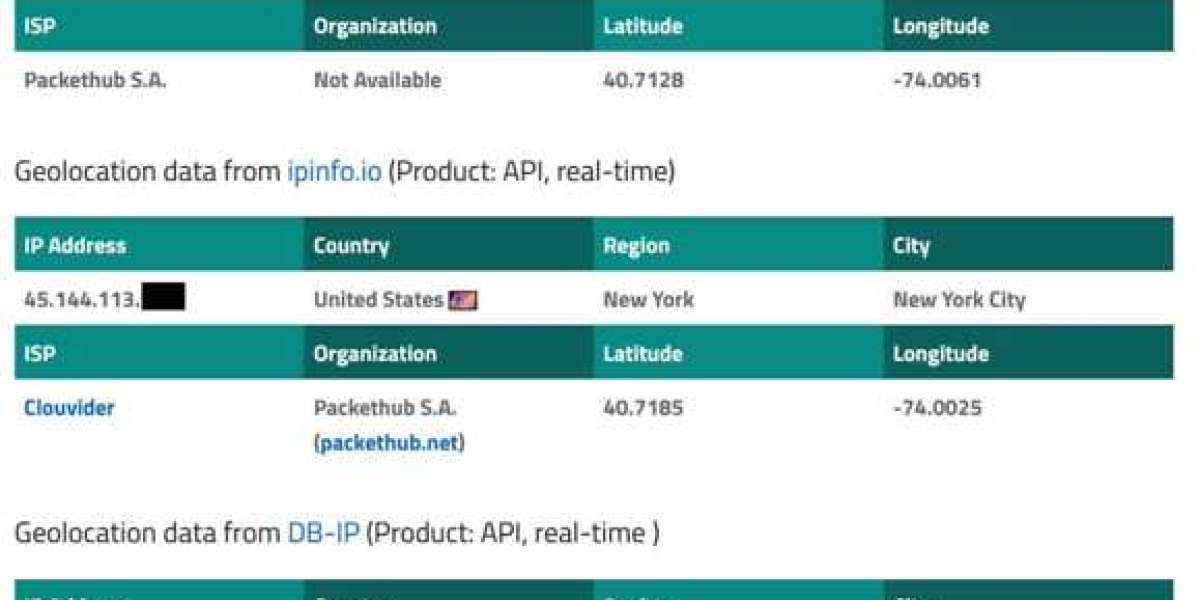
To verify your current IP address, utilizing an online tool is the most efficient approach. While command-line methods exist for different operating systems, they can be cumbersome and vary between Windows, macOS, and Linux.
Many websites provide IP address checks, often including geolocation data. However, results can differ between services. For a comprehensive view, iplocation.net is recommended. This platform checks your IP across multiple databases, effectively highlighting the amount of personal information that is publicly accessible.
To effectively conceal your real IP address, a Virtual Private Network (VPN) is your best option.
VPNs function by encrypting your internet traffic and rerouting it through their servers located in various countries around the globe.
Once you establish a connection, you receive a new temporary IP address, making it challenging for anyone to trace your online activities back to you.
Many VPN providers implement a shared IP address system, meaning multiple users on the same server share the same IP.
This enhances your anonymity, as it becomes nearly impossible to identify which specific user visited a website.
Moreover, your Internet Service Provider (ISP) will not be able to monitor your online behavior.
While they may recognize that you are using a VPN, they cannot see which websites you access or the nature of your traffic.
This is especially beneficial for those who enjoy streaming videos, as some ISPs may throttle bandwidth for users who frequently torrent or stream.
If you want to hide your torrent IP address, follow these simple steps:
- Choose a reliable VPN service (we suggest NordVPN).
- Verify your current IP address at www.iplocation.net.
- Log into your VPN account and select a server in your preferred location.
- Check your IP address again; it should appear different, with updated geolocation information that no longer ties back to you.
NordVPN offers a risk-free 30-day trial, which you can sign up for on their website.
This allows you to experience our top-rated VPN without any limitations for a month—ideal for binge-watching your favorite series or while traveling.
There are no hidden fees; just reach out to customer support within 30 days if NordVPN doesn't meet your needs, and you can receive a full refund.
Begin your NordVPN trial today!When it comes to selecting a VPN, not all services are created equal.
It's essential to explore different options to find one that meets your specific needs.
For those interested in torrenting, we have a comprehensive guide detailing the top VPNs available.
Alternatively, if you're looking to immediately safeguard your IP address from your ISP, consider the following recommendation:
The leading VPN for masking your IP address effectively. Jan 2025When it comes to torrenting securely, NordVPN stands out as our top recommendation.
This VPN service boasts an impressive network of over 5,400 servers across approximately 59 countries, ensuring fast and reliable connections.
Compatible with a wide range of devices, NordVPN allows for up to six simultaneous connections, making it convenient for users with multiple gadgets.
A crucial feature is its no-logs policy, which enhances privacy and security for those who frequently torrent.
Additionally, NordVPN excels in streaming capabilities, providing smooth access to popular platforms such as Netflix, HBO Max, and Hulu.
Getting started is a breeze: simply select your desired subscription plan—whether it’s one month, one year, or two years—and complete the straightforward checkout process.
For those prioritizing anonymity, NordVPN accepts payments in cryptocurrencies like Bitcoin, Ripple, and Ethereum, allowing users to sign up without sharing traditional bank details or credit card information.
If you encounter any issues, 24/7 customer support is available, and the service comes with a 30-day money-back guarantee, giving you the opportunity to try it risk-free.
If you find it doesn’t meet your needs or only require it for a short period, cancelling will ensure you receive a full refund.
Key Features:- Robust security and privacy measures- Kill switch functionality- Support for up to six connections simultaneously- Strict no-logs policy- Dedicated servers for optimized torrenting- High-speed performance- Desktop applications might experience longer connection times occasionally
Rating: 5 out of 5
For those engaged in P2P sharing, NordVPN is particularly well-suited due to its exceptional speeds, comprehensive security features, and capability for streaming.
Unique among its competitors, this provider has had its no-logs policy independently verified on two occasions, further enhancing its credibility.
Additionally, the 30-day money-back guarantee provides peace of mind.
While there are alternative methods to conceal your IP address during torrenting, they often come with more complexity and reduced effectiveness compared to using a VPN.
Proxies, for instance, are typically slower and lack encryption for other applications, which means your ISP could still keep tabs on your activities across different browsers or even tabs within the same browser.
Online Privacy Risks Explained
Your online activities can be vulnerable when using proxies or torrent sites, as the owners may exploit your data. They might sell your information to advertisers or share it with third parties. In contrast, reputable VPN services prioritize user privacy, maintaining minimal logs and resisting governmental demands for user data.
You might assume that connecting to a public Wi-Fi network would conceal your activities due to a different IP address. However, this assumption has significant flaws.
Firstly, many public Wi-Fi networks prohibit peer-to-peer (P2P) traffic entirely. If you manage to bypass this restriction, the owner of the hotspot likely monitors user activity, allowing them to identify which IP address was engaged in torrenting. They may also track the MAC address of your device, linking it directly to your actions. Coupled with the presence of CCTV cameras in such locations, it becomes evident that public Wi-Fi does not offer the anonymity you might expect.
Moreover, public networks are prime targets for cybercriminals due to their lack of robust security measures. Even without torrenting, your data might be intercepted through methods like man-in-the-middle attacks, potentially exposing sensitive information such as login credentials, banking details, or even your home address if you shop online.
When you connect to a VPN, your real IP address is intended to be hidden from both website owners and other torrent users. However, there is still a risk of IP address leaks.
This occurs because there are two types of IP addresses: IPv4 and IPv6. IPv4 addresses look like this: “123.123.123.123”, while IPv6 addresses are more complex, represented as a 32-character hexadecimal string, such as “1231:1e4f:1231:2312:3123:1a2b:1231:2312”.
Currently, most VPNs primarily support IPv4, leaving your original IPv6 address exposed.
The positive aspect is that checking for IP address leaks is simple. Just connect to your VPN and use online tools designed for this purpose. Websites like Comparitech offer IP leak checkers, and alternatives like ipleak.net can also be utilized.When you check your IP address, it might reveal your real location, indicating that your VPN isn't effectively keeping you anonymous. Don't worry; we have solutions to help you out.
To tackle IPv6 leaks, opting for a VPN that automatically manages this for you is the simplest route. For example, NordVPN completely disables IPv6 to safeguard your IP from exposure while you surf the web. Some other VPN services also offer a toggle for IPv6 leak protection, which can be activated in their settings.
If those options are unavailable, you can manually turn off IPv6 on your device. We provide a detailed guide on this in our post about IPv4 versus IPv6.
HTML5 geolocation leaks pose a risk as websites can track your location without your consent. This capability arises from advancements in HTML5, allowing web applications to access your geographical position. Both client-side and server-side scripting can exploit this technology. Although it serves legitimate purposes, it can also enable unauthorized data collection.
For instance, a website might use HTML5 geolocation to ascertain your location and tailor advertisements accordingly. Similarly, applications could monitor your movements, accumulating detailed information about your whereabouts over time. This data can be exploited by malicious entities for targeted attacks or other harmful activities.
To mitigate the risk of HTML5 geolocation leaks, it's crucial to keep your browser updated with the newest security patches. Users should also scrutinize the permissions granted to websites and applications, disabling any unnecessary location-tracking features. Additionally, using a reliable VPN when connecting to public Wi-Fi is vital to ensure your information remains secure.
A Tor exit node marks the final stage in the network of computers that facilitate internet access for users relying on the Tor anonymity network. Typically, these nodes are operated by volunteers who offer their machines for free access to the network. However, any data passing through these exit nodes can be monitored and recorded by the node operator, presenting a security risk for those seeking privacy. Despite this, many users still choose Tor exit nodes for their practicality and dependability.
Circumventing Internet Restrictions
Accessing restricted websites can be challenging, especially in regions where governments impose internet censorship.
Utilizing Tor exit nodes can effectively circumvent these restrictions.
By routing your internet traffic through a Tor exit node situated in a country without such limitations, you can gain access to blocked sites seamlessly.
When it comes to torrenting, it’s important to note that while the act itself is not illegal, downloading copyrighted content can lead to legal complications.
Identifying copyrighted material is often straightforward; if a torrent claims to provide a new movie or popular TV show for free, it’s likely protected by copyright laws.
Conversely, if you’re downloading a film that is in the public domain or available for free, such as Night of the Living Dead (1968), you’re generally in the clear.
Copyright holders typically focus their efforts on those who upload content rather than individuals downloading it.
This is why numerous downloads of new episodes, like those from Game of Thrones , can occur without significant legal repercussions for the downloaders.
It’s crucial to understand that Comparitech does not promote or support any actions that violate copyright laws. Always consider the legal implications and the rights of the original creators before engaging in potentially infringing activities.
Several key terms are commonly associated with torrenting, and understanding them is vital for users:
-
Seeds: Individuals who have completed the download of a file and are actively sharing it with others.
-
Peers: Users who are in the process of downloading a file, sharing parts of it with others during the download.
-
Leeches: Those who download files without contributing back to the sharing pool by uploading.
-
Client: The software application you use to manage and download torrent files.
What is a Netflix VPN and How to Get One
A Netflix VPN is a virtual private network that enables users to access content on Netflix that is restricted to specific regions by connecting to servers in different countries. By choosing a reliable VPN provider that supports streaming, users can create an account, download and install the VPN application, and connect to a server in the desired region to unlock and enjoy a wider array of Netflix content.
Why Choose SafeShell as Your Netflix VPN?
If you're looking to access region-restricted content using a Netflix VPN, consider the SafeShell VPN as an excellent choice. SafeShell VPN addresses common issues like outdated software that might cause a Netflix VPN not to work by offering cutting-edge technology designed to effectively bypass Netflix's detection mechanisms. With high-speed servers optimized for Netflix, you can enjoy seamless streaming of your favorite shows and movies without interruptions, thanks to lightning-fast connection speeds and buffer-free playback.
Moreover, SafeShell VPN allows you to connect up to five devices simultaneously across various operating systems, including Windows, macOS, iOS, and more, ensuring you can enjoy content on any device. The exclusive App Mode feature lets you unlock content from multiple regions simultaneously, providing access to a vast range of streaming services and libraries. With lightning-fast speeds and top-level security through the proprietary ShellGuard VPN protocol, SafeShell VPN ensures an unparalleled streaming experience while keeping your data secure.
A Step-by-Step Guide to Watch Netflix with SafeShell VPN
To begin using SafeShell Netflix VPN , the first step is to subscribe to SafeShell VPN by visiting their website at https://www.safeshellvpn.com /. Choose a plan that aligns with your needs and budget, then proceed by clicking the "Subscribe Now" button. Once subscribed, the next step is to download and install the VPN software on your device. Go back to the SafeShell VPN website, select your device's operating system—be it Windows, macOS, iOS, or Android—and download the appropriate app or software version to install it.
After installation, launch the SafeShell VPN app and log in to your account. SafeShell VPN offers two modes, and for an optimal Netflix experience, it is recommended to select the APP mode. Following this, browse through the list of available servers and select a server located in the region whose Netflix content you wish to access, such as the US, UK, or Canada. Click "Connect" to establish a secure connection to your chosen server. Finally, open the Netflix app or website, log in with your Netflix account, and enjoy streaming content from the region you selected with the help of SafeShell Netflix VPN.